dashboard
Kubernetes的子项目之一,是Kubernetes核心附件之一。作为Kubernetes的Web用户界面,用户可以通过Dashboard在Kubernetes集群中部署容器化的应用,对应用进行问题处理和管理,并对集群本身进行管理。通过Dashboard,用户可以查看集群中应用的运行情况,同时也能够基于Dashboard创建或修改部署、任务、服务等Kubernetes的资源。通过部署向导,用户能够对部署进行扩缩容,进行滚动更新、重启Pod和部署新应用。在Kubernetes 1.8之后,在部署dashboard时,有着更复杂的权限检查了。传统的在互联网上看到的开放访问的方式不一定支持了。
安装部署dashboard
打开 dashboard github地址,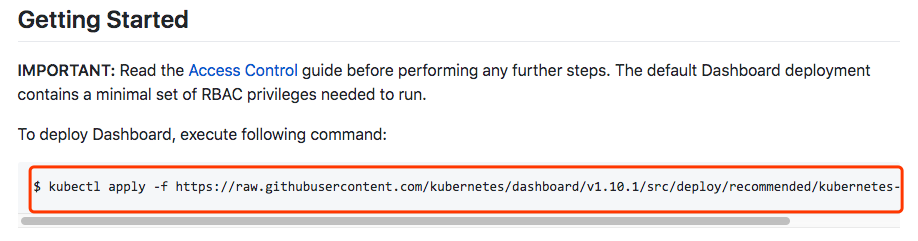
我这里把这个yaml文件下载下来,这样可以看看里面的内容,然后进行安装。
如果dashboard镜像拉取不下来,可以如下操作:
dashboard自身是https的,可以查看yaml中定义的Service: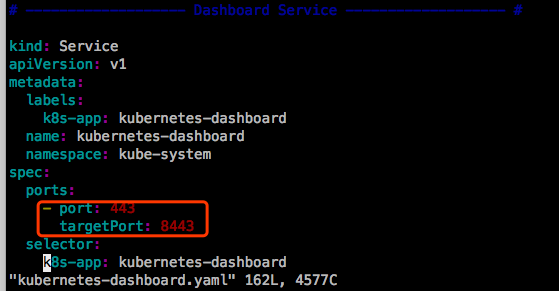
并且这个Service的类型是默认的cluserIP类型的,可以改为NodePort类型的:
浏览器输入:https://172.16.206.32:30763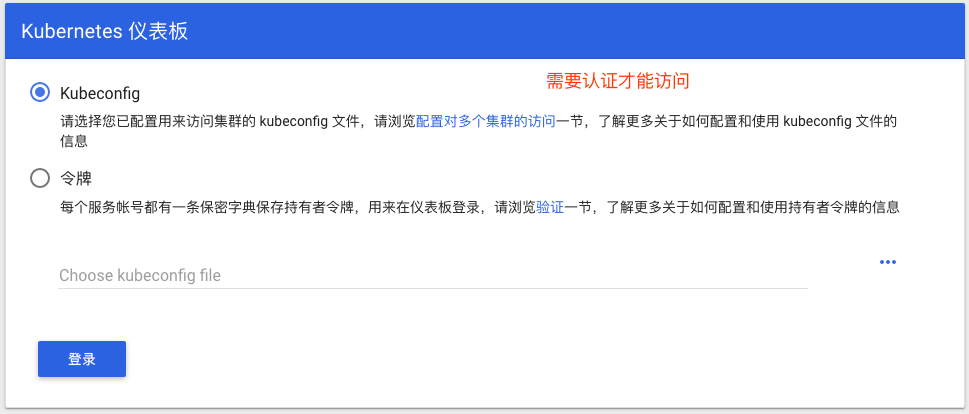
- 令牌认证可以直接输入令牌。
- Kubeconfig:kubectl就能使用kubeconfig,但是注意认证时必须使用serviceaccount账号认证。dashboard自己是个Pod,我们所提供的信息是让dashboard Pod认证到k8s集群上去的。不是让我们自己认证,是让dashboard Pod认证k8s,因为我们是通过这个Pod去访问管理集群上的Pod的。因此我们是为dashboard这个pod提供一个kubeconfig,所以主体必须是一个serviceaccount。
token认证
token认证也需要先定义一个serviceaccount。
接下来需要通过RoleBinding把dashboard-admin这个serviceaccount和集群管理员绑定起来。不然这个serviceaccount不能通过RBAC的检查。dashboard部署完后,登录进来期望借助于dashboard做什么事情,假如要做整个集群的管理,也就是说该serviceaccount应该具有整个集群的访问权限,那么就应该通过ClusterRoleBinding把这个serviceaccount和cluster-admin角色绑定在一起。
绑定完成后,我们去获取对应的serviceaccount的secret信息。并且通过这个secret就可以访问集群了。
这个 dashboard-admin-token-9sbkc 是上面创建serviceaccount时自动生成的。
这个token信息就是当前 dashboard-admin 这个serviceaccount的认证令牌。
在浏览器dashboard的登录界面,选择”令牌”,然后将上面的token信息复制上去,点击”登录”。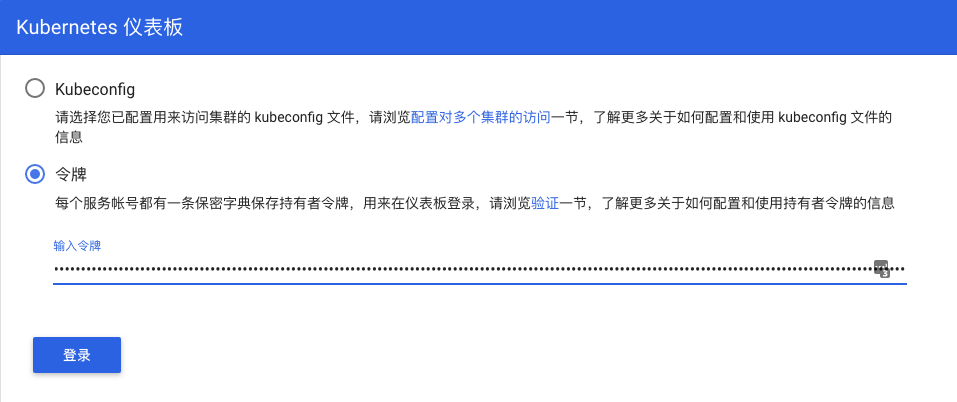
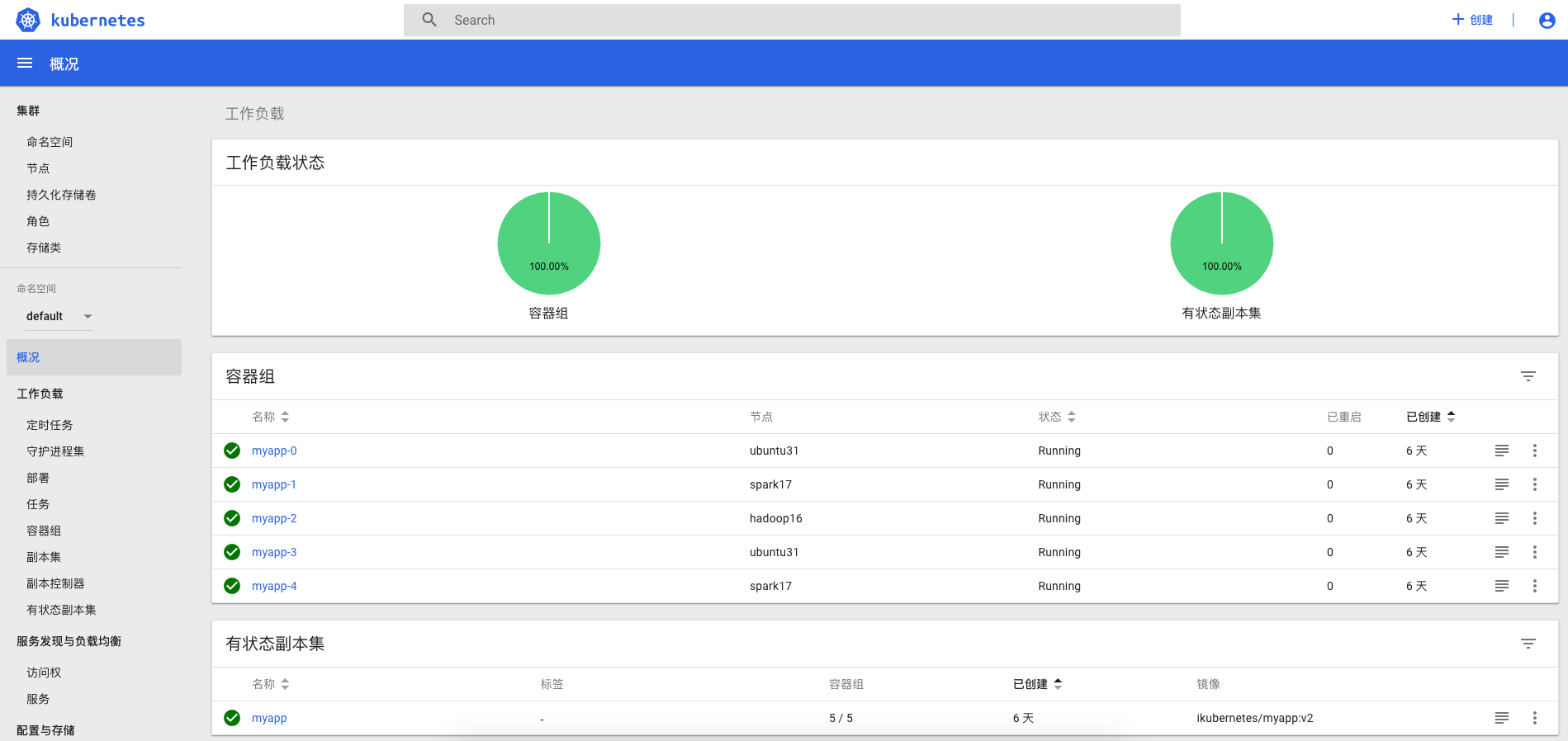
登录进来了,可以查看所有的名称空间。
Kubeconfig认证
这里创建个权限小一点的,只让它对默认名称空间有权限的管理员。还得在创建个serviceaccount。仅能够通过dashboard访问default一个名称空间,不让他做分级管理。所以需要把这个serviceaccount绑定在admin上,admin也是ClusterRole。但是可以使用RoleBinding去绑定。
|
|
使用这个token去登录dashboard,只能管理default名称空间的资源。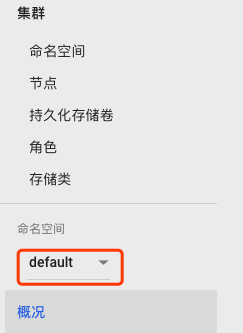
但是我们希望使用装载一个kubeconfig配置文件来认证,所以接下来不得不为这个serviceaccount创建一个配置文件。配置文件和之前kubectl配置文件基本一致。注意去设置的时候要放上面看到的token,不要放证书进去,证书只是为了做k8s系统认证的。
需要把 token 写到kubeconfig中。使用token进行认证。注意在设置认证token时不要把加密后的token设置进去,直接写入上面看到的那个token。
查看生成的配置文件:
将配置文件传到自己本地,然后在dashboard界面选择kubeconfig认证,使用该配置文件认证: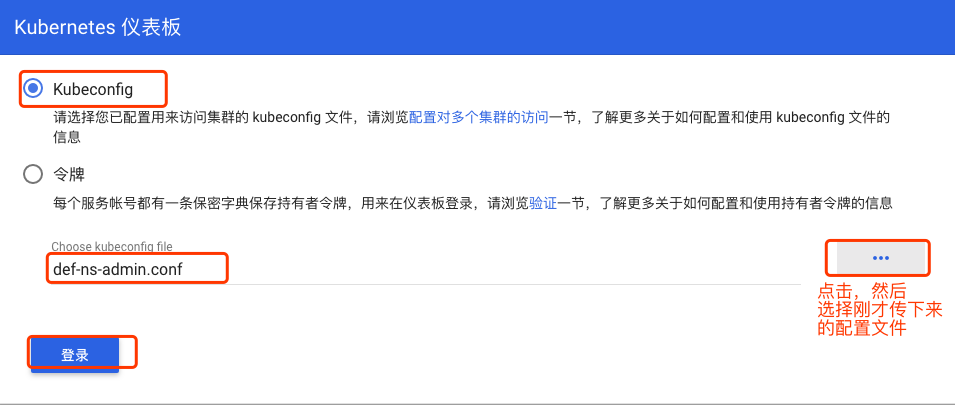
以后可以使用dashboard来管理资源了,比如创建资源:
【总结】:
认证时的账号必须为ServiceAccount: 被dashboard pod拿来由kubernetes进行认证;
token认证:
(1)创建ServiceAccount,根据其管理目标,使用rolebinding或clusterrolebinding绑定至合理role或
clusterrole;
(2)获取到此ServiceAccount的secret, 这个secret是创建serviceaccount自动生成的。作为此serviceaccount去k8s认证的信息。查看secret的详细信息, 其中就有token;
kubeconfig认证: 把ServiceAccount的token封装为kubeconfig文件
(1)创建ServiceAccount,根据其管理目标,使用rolebinding或clusterrolebinding绑定至合理role或clusterrole;
(2)kubectl get secret | awk ‘/^ServiceAccount/{print $1}’ ##这里的ServiceAccount指的是你创建的serviceaccount的名字
KUBE_TOKEN=$(kubectl get secret SERVCIEACCOUNT_SERRET_NAME -o jsonpath={.data.token} | base64 -d)
(3)生成kubeconfig文件
